Shit happens and you may one day be faced with your account being compromised: your private keys have been leaked or stolen and your account and funds are at risk.
Fortunately, each account on the Hive blockchain is linked to a recovery account that can reset the compromised account owner key, enabling its original owner to update it with a new password and keys.
How is the recovery process working?
- You generate a new password and a set of related private and public key pairs.
- You ask the recovery account to reset your password by providing him with the new public owner key.
- The recovery account initiates the change of your credentials
- You have 24 hours to confirm the change.
This post will not explain in detail how to perform these operations but explain what problem may arise and the solution I propose to remedy it.
For details on how to deal with the recovery process, you can read this excellent post written by @abitcoinskeptic. Although a bit outdated, it remains very educational.
The Recovery Account - A trusted cornerstone
What is the Recovery Account?
The recovery account is another Hive account that is able to initiate the recovery of your account, in case you solicit it after your account has been compromised. For the recovery to be possible, you often need to go through a process. On Steemit, Inc. you need to send them a recent password for your account, used no longer than 30 days ago. More information will be required to determine that you are the rightful owner.
What is the role of the Recovery Account?
The duty of the owner of the recovery account is to make sure whoever is asking for the account recovery is the real owner of the account to be recovered before initiating the account recovery procedure.
What if the Recovery Account does not initiate the recovery process?
You’re fucked! This account is the only one to be able to initiate the recovery process.
As you can see, without the recovery account performing steps 3 of the recovery process, it is impossible to finalize the process of resetting your owner key.
Why would the Recovery Account holder not initiate the recovery process?
There can be lots of reasons for this.
- Its owner might not be able to verify you’re the real owner of the account to be recovered
- Its owner might be not responding (unreachable or even dead)
- Its owner might ransom you to perform the task
- You cheated on the owner with his wife or husband and now he/she takes revenge by refusing to comply.
… and many other reasons.
Joking aside, I think that cases 1 and 2 are the most likely, point 2 is the one with the most risk factor.
Many of the accounts on the Hive blockchain have been created by Steemit, inc and still have @steem as their recovery account. Not sure many of us still trust them as a recovery account.
This is also an issue for accounts that are created by regular users who have claimed account tickets using their unused resource credits and are using them to create accounts for others.
When they create an account using their available tickets, they are set by default as the "recovery account". A responsibility maybe they didn't know they have, didn't ask for and don't want. Some may become inactive over time or will be unreachable when someone needs them to recover their account.
Then there's a problem.
How to mitigate these risks
The choice of your Recovery Account is therefore of paramount importance. You need a trusted but, even more, reliable person who:
- is able to identify you with certainty.
- you can reach anytime in the future.
Changing your recovery account from @steem to @hive.io will not solve our issue. Mainly because hive.io is not a single entity that can be fully "trusted" even if the majority of people who are involved in its development are trustworthy people. It is also not “reliable” because no structure has been put in place to ensure such service and availability 24x7.
This is where Hive Recovery comes in.
Hive Recovery is a service that I have set up to work uninterrupted and is completely autonomous.
Navigate to https://tools.hivechain.app/recovery
It’s a very simple webpage where you can securely define @hive.recovery has your recovery account and secure your (future) recovery process.
A - How to configure the recovery account?
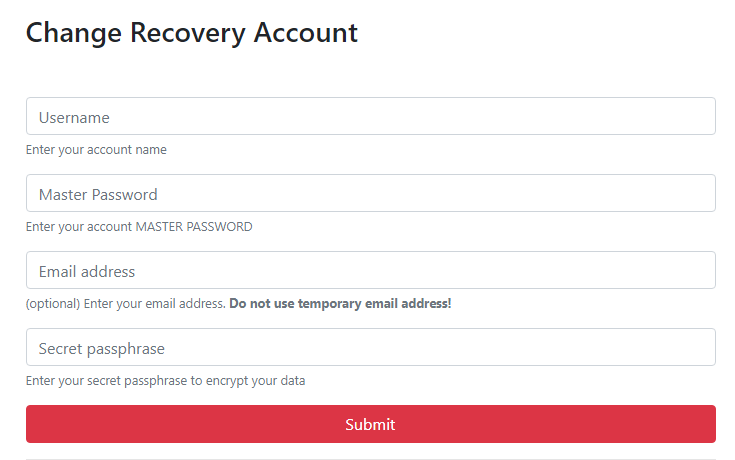
Fill the form with:
- your username (without the
@) - your Master Password (read below why it is asked for)
- your email address. This is optional but will add more security to the recovery process (more on this later in this post)
- a secret passphrase that you and only you will know (a very cool online passphrase generator can be found here)
Once ready, click on the Submit button
At this step of the process, the web page will encrypt your account name and email address (if provided) using your passphrase (let’s call the result of this encryption E1).
The web page will then
- encrypt the E1 once more using both your memo key and @hive.recovery memo key and insert it in the memo of a micro-transfer
- change your recovery account to @hive.recovery
Both operations are performed atomically, which means that if one of the operations fails, neither of them is recorded on the blockchain.
Confirm the broadcasting of the operations and you’re done.
You will need it later if you ever need to recover your account!
After setting up your @hive.recovery as your recovery account, you have to wait 30 days before @hive.recovery will become your recovery account and before you can initiate a recovery. This is to ensure that someone gaining access to your account cannot update the recovery info to his/her own advantage then initiate the recovery process and lock you out.
Why do you need my Master Password?
You Master Password is used to retrieve
- your private owner key: this key is mandatory to issue the
change_recovery_accountoperation to the blockchain. One bird two stones, it will also be used to send the (micro)transfer operation. - your private memo key: this key will be used to encrypt the memo of the above-mentioned transfer.
Your Master Password or Private Keys will NOT been stored or sent over the internet by the Account Recovery Setup process!
B - How to recover my account?
You can only initiate a request to recover your account at least 30 days after performing the previous step since it is only from this moment that @hive.recoverywill officially be your recovery account.
So, let's say your account has been unfortunately compromised and it’s now time to recover it.
Navigate to https://tools.hivechain.app/recovery and go to the second part of the page
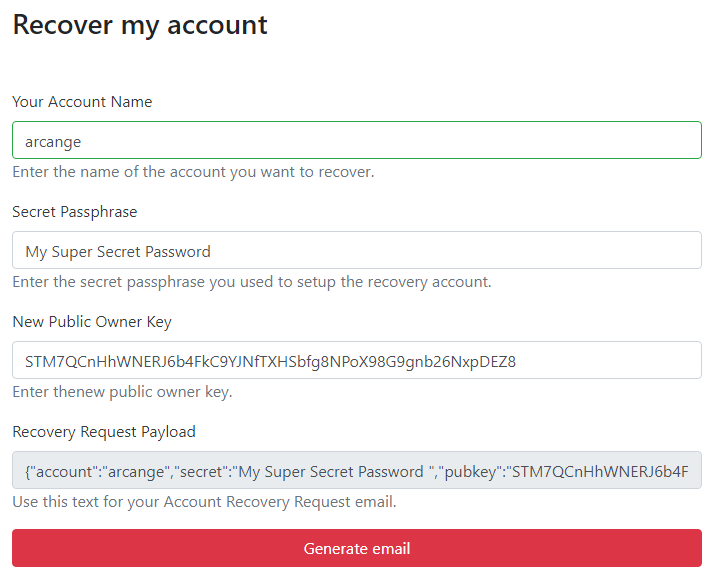
Fill the form with:
- Your username (without the
@) - The secret passphrase you have used to configure your recovery account (step A).
- The public owner key from a new password and keys set you previously generated for your account (more on this below)
Then click on the “Generate Email” button. This will trigger your default email client to create a new email ready to send with pre-filled “to”, “subject” and “body”.
If your email client does not open, you can send an email manually to recovery[at]hivechain.app and copy the Recovery Request Payload text in the body of your email. The subject doesn’t matter. You can put what you want there.
WARNING: If you provided an email address to your memo when setting up the recovery account, you must send the email from the same email address!
When receiving your email, @hive.recovery will parse this payload and:
- verify it is the recovery account of the provided account
- search for the micro-transfer with the encrypted memo
- verify it can decrypt the memo using the provided passphrase
- verify if the account name in the email matches the account name in the decrypted memo
- if an email address has been provided at step A, verify if the email address used to send the payload is the same as the email address in the decrypted memo.
If all these tests pass through, @hive.recovery will then initiate the recovery procedure using the new public owner key
The last thing you will need to do is confirm the recovery request within 24 hours.
How secure is this service?
Considering your account is safe when doing step A, you are the only one to be able to make the micro-transfer using your active key and encrypt information using your memo key. If a hacker changes your password, your keys will change too. This way, @hive.recovery can identify you with certainty.
Also, remember that a double encryption process is used:
- encryption of your data using your passphrase -> E1
- encryption of E1 using memo keys -> E2
With this double encryption process in place, only you and @hive.encrypted can access E2 and read E1, but @hive.encrypted cannot decrypt E1 because it has not your passphrase. No one, including @hive.recovery, can ever read the content of E1 until you provide the passphrase to decrypt it.
Even if a malicious actor finds your passphrase, he/she won’t be able to access E1 because he/she will need your private memo key to decrypt E2 first.
An attacker would need you to get your passphrase AND your memo key (AND optionally your email address and its control) to be able to lock you out of the recovery process.
On the other hand, if these are safe and if @hive.recovery can decrypt E1 and the information it contains matches your data, then it can identify you with certainty and safely initiate the recovery process for you.
A bit about privacy
The only private element that you communicate to @hive.recovery (and therefore to me) is an email address. For obvious reasons, this email address cannot be temporary. We can therefore consider that you could potentially be identified with this email address.
However, remember that this information is encrypted using your passphrase. So no one who does not have this passphrase has access to it. This is also the case for @hive.recovery and me, who will only be able to access it from the moment you initiate a recovery procedure
For the most paranoid of you who still would not trust me, which is perfectly acceptable, you can freely not use this option. It is only provided to add an additional level of security.
Make your own research
The webpage is hosted on https://tools.hivechain.app/recovery
Do not run it from an untrusted website
Exercise due diligence (you should not trust me 😉).
Source code available on Github. You can download and run it locally.
UPDATE:
Several people have rightly pointed out to me that the Hive Keychain extension doesn't work when the webpage is not hosted on a remote server. Therefore, I decided to remove the Hive Keychain integration so that it can now be run entirely locally and without having to use a third party.
The good news is that it will also solve the issue of people who felt left out because they use Hivesigner.
The only drawback is that you must now enter sensitive data. Therefore, please be cautious and double-check where you are running the page from and, if possible, audit the code you are running.
Support
Support for this service is provided on Hivechain.app server on Discord. Use the dedicated Account Recovery dedicated channel.